Start a Bug Bounty program
Bug bounty programs are a wonderful tool to complement penetration testing. Defining, setting up and managing such a program involves many challenges - we know the perspective of both the "ethical hacker" and the responsible program manager.

Why Bug Bounty Programs Work for Modern Companies
Traditional security audits test at fixed intervals. A Bug Bounty Program complements these measures with continuous testing by highly motivated researchers and ethical hackers. You benefit from the experience of international specialists without having to manage the operational effort yourself - we translate every finding into prioritized actions for your team.
- Faster detection: Critical exploits and zero-day vulnerabilities become visible within hours instead of after the next audit.
- Cost control: You only pay for valid findings and keep your budget under control through tiered reward models.
- Compliance assurance: Traceable reports help with requirements from NIS2, ISO 27001, TISAX, or internal audit programs.
Together we define which assets need protection, how sensitive data is, and what maturity levels already exist in your organization. Then we make fact-based decisions on whether a program scales or whether complementary measures like penetration testing or eASM make more sense initially.

Program Guardrails & Platform Setup
Maturity Workshop
Business Case & Risk Assessment
Policy & Researcher Selection
Launch Playbook
Developer Enablement
Quick Fix & Hardening Support
Continuous Monitoring Services
Triage & Retests
Communication & Prioritization of Findings
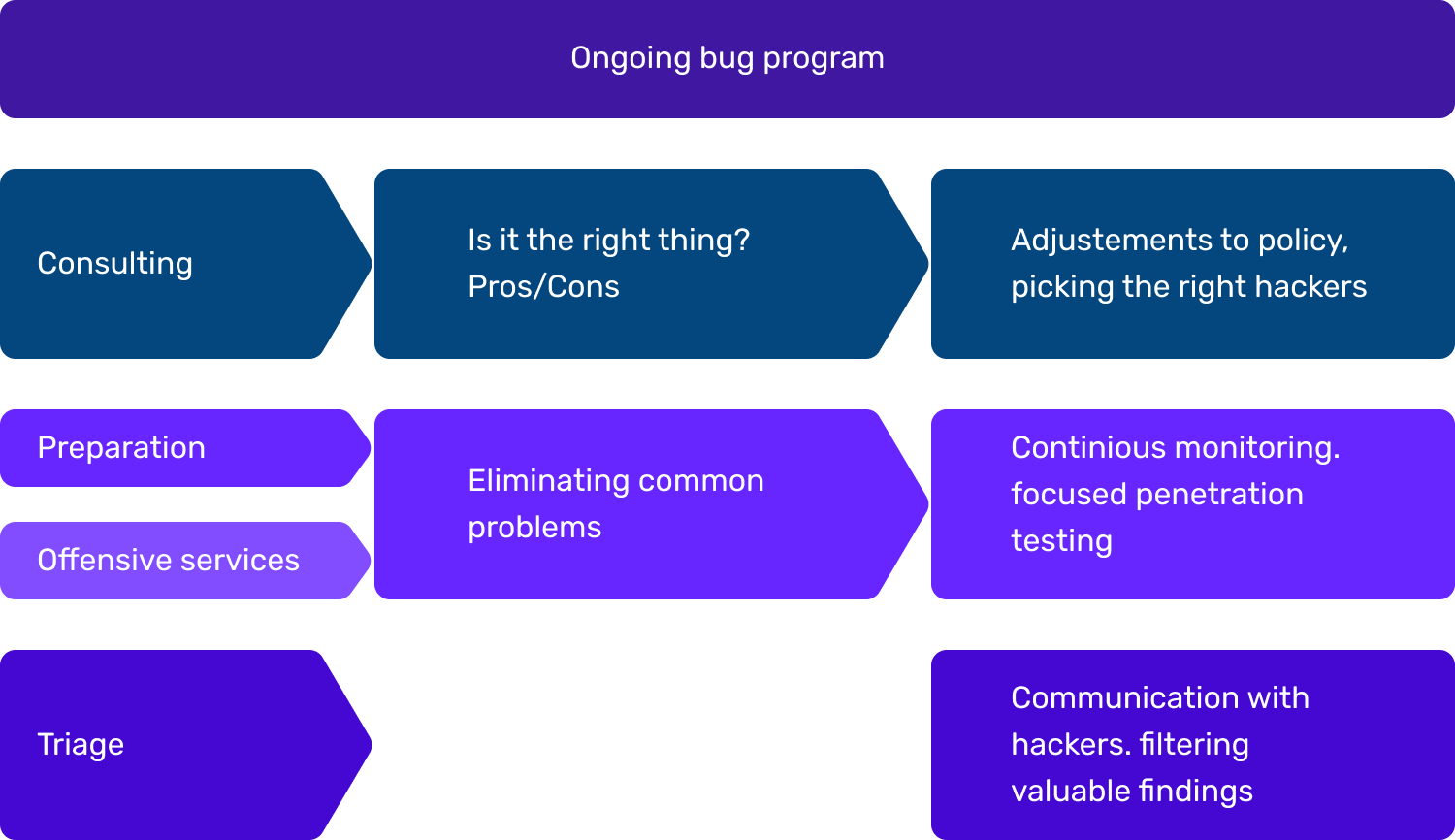
Approach to Setting Up a Bug Bounty Program
Our approach combines strategic consulting with operational relief. We structure your program so that budget, resources, and security goals align - without surprises in governance, developer capacity, or internal approval processes.
Scoping & Business Case
We jointly evaluate goals, risk appetite, and existing security processes. From this, we derive which assets should be in scope, how governance should look, and whether alternative measures need to be implemented first.
- Stakeholder workshop and maturity check
- Definition of assets, exclusions, and success criteria
- Reward model including budget and approval process
Program Setup & Launch
We create policies, communication channels, and guidelines for researchers. If needed, we close preparation gaps through penetration testing, shadow IT discovery, or hardening sprints.
- Hand-picked selection of vetted researchers
- Onboarding package including safe harbor, response times, and SLA templates
- Tooling setup for platform, ticketing, and internal reporting
Managed Triage & Improvement
We handle the evaluation of all findings, prioritize actions, and support development teams through retest. Dashboards and management updates make the impact transparent at all times.
- Technical triage including proof-of-concept verification
- Coordinated communication and reward process with researchers
- Reporting on MTTR, finding quality, lessons learned, and optimization steps
Get in touch
Have questions about our services? We'd be happy to advise you and create a customized offer.
Quick Response
We'll get back to you within 24 hours
Privacy
Your data will be treated confidentially
Personal Consultation
Direct contact with our experts

Complements Bug Bounty Consultation
Continuous Monitoring
Our eASM platform "Argos" continuously monitors your external attack surface. Findings flow directly into the Bug Bounty policy - ensuring that only current and approved systems are in scope.
Penetration Testing
Penetration testing provides clarity before you go live. We close critical gaps in core systems and ensure your Bug Bounty budget isn't depleted on basic findings.
Darknet Intelligence
Attackers use leaked credentials as entry points. With Darknet Intelligence, you can detect whether compromised accounts could impact the Bug Bounty program - and react before researchers or real attackers exploit them.
What clients say about us
Experiences from real projects
„I've been really impressed with DSecured. The results they delivered exceeded our expectations. They found a wide range of IT problems and severe vulnerabilities and always communicated clearly. Working with them has been straightforward and reassuring.“
„The security of our customers’ data is our top priority. Thanks to DSecured, we were able to improve the resilience of our systems and realize how important the topic of "Shadow IT" is. The commitment of the team and their skills made the crucial difference for us.“
„DSecured was able to discover a surprising number of previously undetected security gaps in our infrastructure. The Argos platform as well as classic penetration testing were used for this. We really appreciated the honest advice on the subject of IT security and automation and would like to thank Mr. Strobel for this.“
„Mr. Strobel and his team regularly carry out penetration tests against our automation platform - and always find what they are looking for. The results are presented clearly and reproducibly. Communication has so far taken place via short channels, for example via Slack. We can definitely recommend DSecured.“

