How We Work
At DSecured, we rely on a structured and transparent penetration testing process. From the first inquiry to the final report, we support you with clear communication and cutting-edge tools.
Our secure client dashboard gives you real-time insight into progress and all results at any time.
Our Penetration Testing Process
From initial request to final report - we guide you through every step transparently and professionally
Quote
You contact us via our contact form, the configurator, or directly by email/phone. We create a customized quote based on your specific requirements and project scope.
Contract
After accepting the quote, we send you the service contract including NDA. All legal framework conditions, liability issues, and responsibilities are clearly defined.
Scoping
In the scoping call, we jointly define the exact test scope: Which systems, which functions, which test methods? We clarify technical details, access credentials, and set up test accounts.
Kick-Off
The official project start: We set up your dashboard, distribute access credentials, and introduce our team. You receive all necessary information for the test phase.
Testing Phase
The actual pentest phase begins. Our experts systematically test your systems for vulnerabilities. You see all findings live in your dashboard and can ask questions or comment at any time.
Reporting
After completing the tests, we create a comprehensive report with all findings, including risk assessment, technical details, and concrete solutions. The report is available for download in the dashboard.
Retesting
After you've fixed the vulnerabilities, we conduct retesting to verify successful remediation. This is included in the price and ensures all issues have been resolved.
Attestation
After successful retesting, we provide you with an official attestation confirming the successful completion and remediation of all critical vulnerabilities - perfect for compliance and audits.
Important to Know
Throughout the entire process, we are available to you via various communication channels. Our goal is maximum transparency and smooth collaboration.
Our Client Dashboard
Your personal access to all pentest information - secure, clear, and available anytime
Maximum Security & Compliance
Our client dashboard runs on secure German servers - not a cloud service. Password-protected, encrypted, and meeting the highest compliance standards.
Infrastructure & Access
- Hosted in Germany (GDPR compliant)
- SSL/TLS encryption
- Password-protected access
- No cloud - Full control
Data Encryption
- All vulnerability details encrypted
- Public/private key after project completion
- Private key never on the server
- GDPR & NIS2 compliant
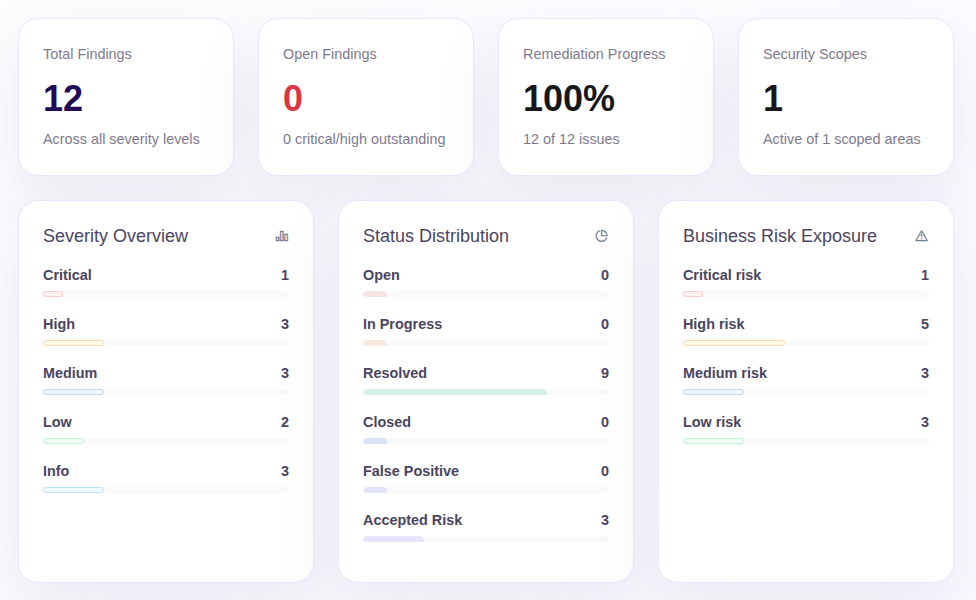
Header & Statistics
The dashboard header shows you the most important metrics at a glance: Number of vulnerabilities found by criticality, current project status, timeline, and test progress.
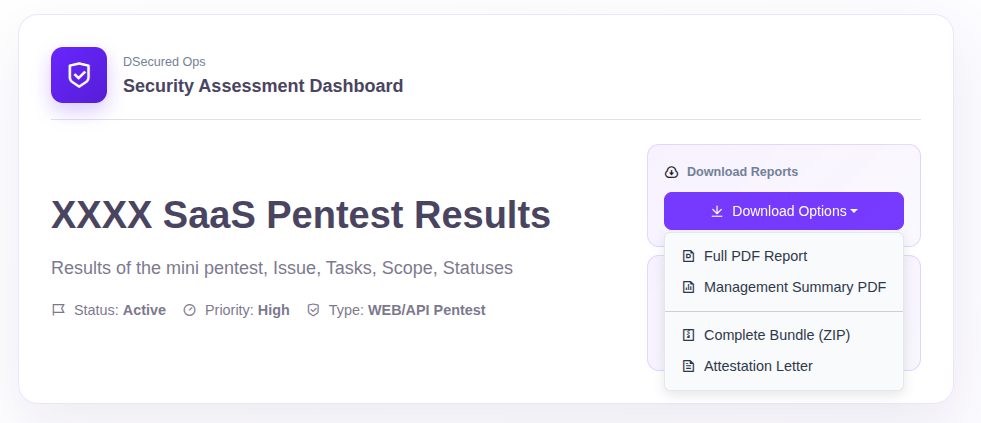
Downloads & Reports
Download all relevant documents anytime: the final pentest report, executive summaries for management, attestations for audits, and technical details for your developers. Everything in one place.
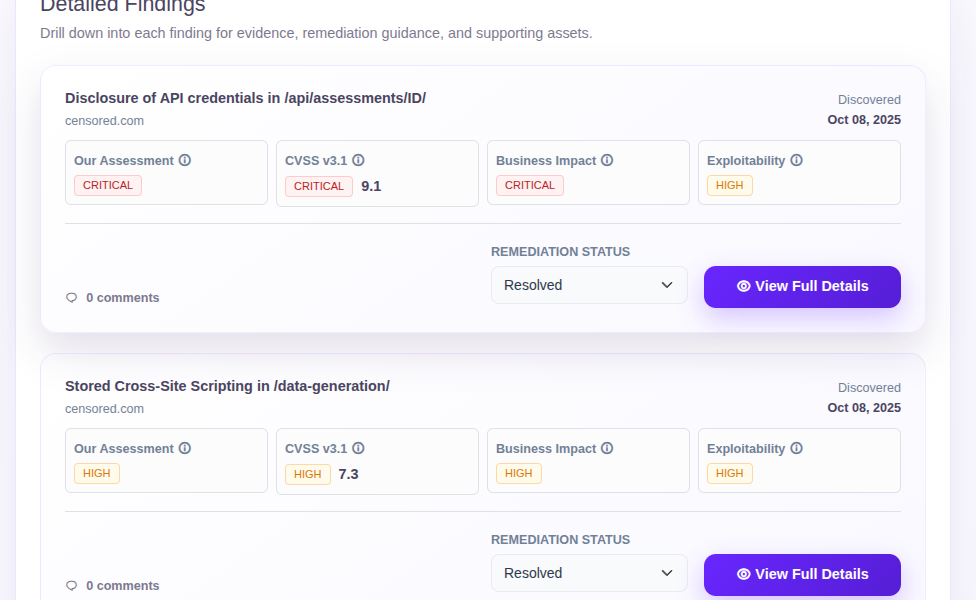
Issue Overview
All found vulnerabilities clearly listed. Filter by criticality, status, or category. See at a glance which issues have been fixed and which are still open.
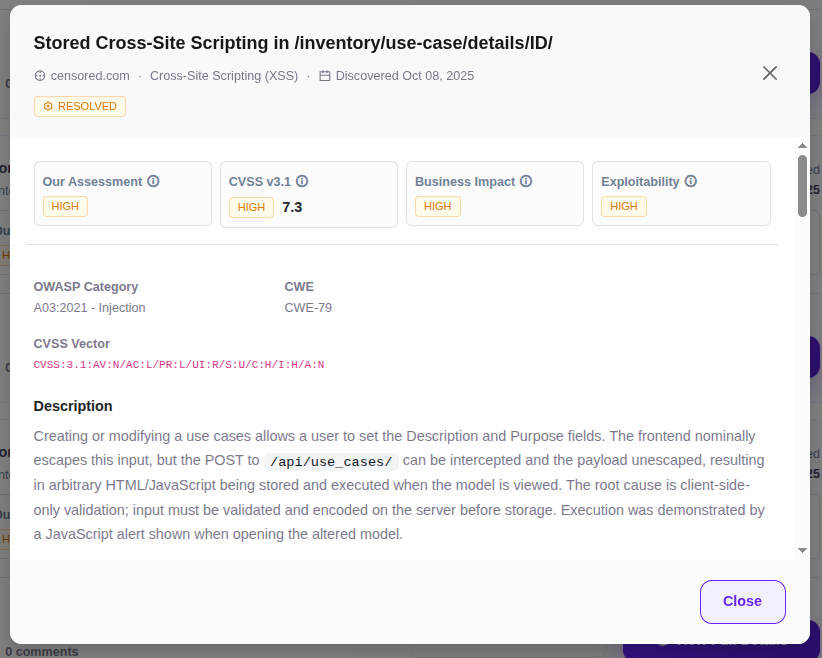
Detailed Issue View
Each vulnerability is thoroughly documented: technical description, risk assessment (CVSS), proof of concept, affected systems, and concrete remediation recommendations.
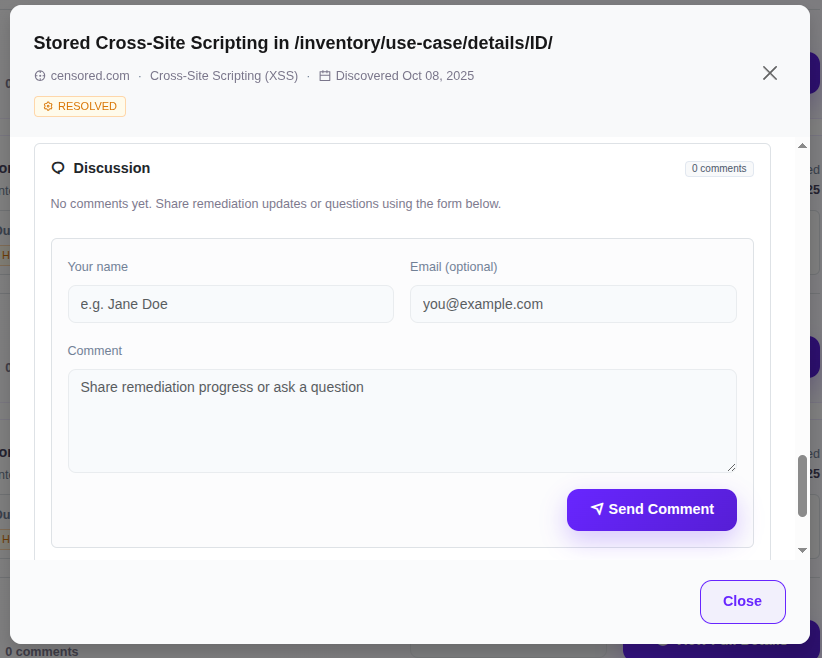
Comment Function
Ask questions directly on each issue. Our team responds promptly and you can discuss with your developers. All communication remains documented and traceable.
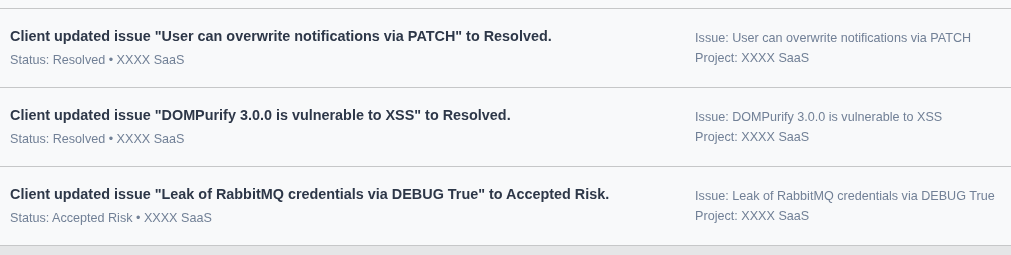
Live Updates
Receive notifications when new vulnerabilities are found, when our team responds, or when status changes. You're always up to date - without having to constantly check.
Dashboard Benefits
Transparency
See at any time what we find and the current status
Save Time
No more Excel lists or email ping-pong
Collaboration
Your entire team can access and collaborate
Compliance
Perfect for audits and certifications
Communication During the Pentest
We use the communication channels you prefer - flexible, fast, and direct
Your Communication Channel, Your Choice
We adapt to your preferences. Already using Slack or Google Chat? Perfect - we'll set up a shared channel. Prefer email or Microsoft Teams? No problem, we're flexible.
-
Direct Contact
Chat directly with our pentesters during the test
-
Quick Responses
Questions are answered promptly, usually within a few hours
-
Documented
All important agreements are recorded in the dashboard
Communication Best Practices
Dedicated Contact Person
You have a dedicated contact person on our side - usually the lead pentester of the project. So you always know who's responsible.
Regular Updates
For longer tests, we automatically provide interim updates on progress. You don't need to ask - we'll contact you proactively.
Critical Findings Immediately
When we find critical vulnerabilities, we inform you immediately - not only in the final report, but right away via chat or phone call.
Flexible Availability
During the test phase, we're available during your regular business hours. In emergencies, also outside of that - we're here for you.
Typical Communication Flow During the Test
We start the chat, introduce the team, and clarify final questions
Brief status updates on progress and new findings
You ask questions about findings or technical details - we respond promptly
Summary, outlook on reporting, and next steps
Your Preferences Matter
During the scoping call, we discuss your preferred communication channels and times. Some customers want daily updates, others only want to be contacted for critical findings. We adapt completely to your needs.
Start Your Penetration Test with DSecured
Experience a transparent, professional, and efficient pentest process. With our structured approach, secure client dashboard, and flexible communication, you're always informed and in control.
Frequently Asked Questions
Answers to the most important questions about our pentest process.
Browse FAQ