Pentest Report: Example of our reports

Structure of a Classic Pentest Report
A pentest report is a document that summarizes the results of a penetration test. On this page you will find a sample report that we regularly update and is based on a real report from 2018. This will give you a good impression of our work and methodology.
The basic structure of our reports is as follows:
- Cover Sheet
- Table of Contents
- Management Summary
- Introduction
- Scope
- Methodology
- General Recommendations
- Overview of All Relevant Vulnerabilities
- Conclusion and Recommendations
What You Get from the Report
Management Summary
On one to two pages, we present risks, business impact, and immediate actions - perfect for executives, CISOs, and audit teams.
Confirmation Letter
For customers or partners, we create an official compliance letter upon request, including test period and scope.
Action Plan
Prioritized action list with responsibilities and recommended deadlines - directly importable into your ticketing system.
Retest Report
After implementation, we repeat the tests and clearly document which findings have been closed, mitigated, or remain open.
How We Present Results
Each entry in the sample report follows a consistent structure - so security, development, and management can quickly understand the context and take action.
CVSS 3.1 score, affected assets, access requirements, and comprehensible impact.
Proof-of-concept, screenshots, and payloads - including notes for log correlation and detection.
Specific fix recommendations, priority, and assignment to responsible teams or vendors.
Methodology
Our methodology is based on industry standards such as the OWASP Web Security Testing Guide and the recommendations of the German Federal Office for Information Security (BSI). We are also familiar with standards such as OSSTMM and PTEST.
In general, for us a penetration test is ALWAYS a manual pentest of a system. Automated tools and methods serve as support to increase efficiency and ensure that we do not overlook any obvious problems. We rely on a combination of manual and automated tests to achieve the best possible results.
The methodology is adapted depending on customer requirements and needs. For example, we may pursue a Red Teaming approach to holistically test the security of a company.
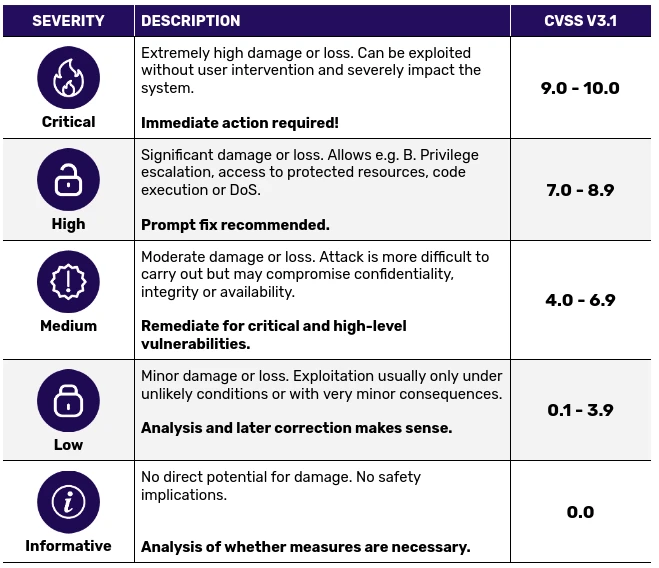
CVSS 3.1 as Scoring System
CVSS stands for Common Vulnerability Scoring System and is an industry standard for assessing the severity of vulnerabilities. CVSS 3.1 is the latest version and was published in 2019. We will likely switch to CVSS 4.0 in the near future and update this page and our sample report accordingly.
More Than a List of Findings
General Recommendations
We formulate best practices for operations, architecture, and DevSecOps - even beyond the tested scope.
Roadmap & Priorities
Recommendations are sorted by impact and effort. Teams immediately know where to start.
Conclusion & Lessons Learned
In conclusion, we show trends and recurring patterns - the foundation for sustainable security initiatives.
Request a penetration test
Have questions about our services? We'd be happy to advise you and create a customized offer.
Quick Response
We'll get back to you within 24 hours
Privacy
Your data will be treated confidentially
Personal Consultation
Direct contact with our experts

