Django Security Check
For standard Django apps
- Settings & configuration audit
- Basic OWASP Top 10 testing
- Template security & XSS check
- Quick ticket-based reporting
With our comprehensive Django penetration testing services, we identify and mitigate security flaws, safeguarding your applications from potential cyber-attacks. Our expert team employs advanced techniques to thoroughly assess all aspects of your Django framework, ensuring your infrastructure remains secure and resilient. Trust us to deliver precise and actionable insights to bolster your application's defense mechanisms.

What we test in Django projects
Serializers, ViewSets, Permissions and Authentication Backends - with focus on Authorization Bypasses.
DEBUG mode, SECRET_KEY handling, ALLOWED_HOSTS and Middleware configuration in Production.
QuerySet security, Raw SQL Injections and insecure filter parameters in Custom Queries.
Django is the Python framework for data-driven web applications - with the boom of LLM/AI, Django has gained massive popularity. The framework defaults are solid, but custom code, REST APIs and inexperienced developers regularly lead to critical vulnerabilities: from DEBUG=True in production to authorization bypasses and SQL injections in raw queries.
Django REST Framework Security We test permissions, serializer validation, ViewSet authorization and custom authentication - 70% of Django projects use DRF, and this is where authorization bypasses emerge.
Configuration & Debug Mode Issues DEBUG=True in production, SECRET_KEY in Git, insecure CORS settings or missing security middleware - we systematically review settings against production best practices.
ORM & Query Security Raw SQL injections, insecure filter parameters and QuerySet leaks - we analyze custom queries, admin panels and export functions for injection vectors.
We deliver prioritized results with code examples, concrete fix suggestions for your dev team and - if desired - management summaries for stakeholders and compliance audits.
{{ question.description }}
{{ addon.description }}
Leave us your contact details so that we can send you a non-binding, customized offer.
Your data will be treated confidentially and will not be passed on to third parties.
A large part of the internet is based on websites and web applications.
Modern websites and SPAs usually communicate with some kind of API.
Fully automated vulnerability scanning for your IT infrastructure or application.
Django pentests uncover framework-specific vulnerabilities - from configuration issues to DRF permission bypasses and ORM SQL injections.
The classic: DEBUG=True in production reveals the entire attack surface - including settings, middleware stack, environment variables and database credentials. We systematically review settings.py against production best practices.
Django REST Framework: Missing or incorrectly implemented permission classes, insecure ViewSet permissions and authorization bypasses through custom authentication. We test granularly whether users can really only access their own resources.
Django ORM is secure - but raw queries, .extra(), .raw() and custom SQL in views regularly lead to SQL injections. Especially with filter parameters, exports and admin panels we find insecure queries.
SECRET_KEY in Git repos, .env files in production roots or insecure ALLOWED_HOSTS lead to session hijacking and CSRF bypasses. We review environment handling and secret management.
Despite auto-escaping in templates: Custom template tags, mark_safe() and JSON rendering lead to XSS. Missing CSRF tokens in custom forms or incorrect @csrf_exempt usage enable CSRF attacks.
Pickle deserialization in session backends, insecure YAML parsing or eval() in custom code - rare, but critical. We analyze deserialization vectors and custom middleware for RCE potential.
70% of our Django pentests include DRF - we combine Swagger/OpenAPI export with custom tooling for efficient API security testing.
Django REST Framework can be exported as Swagger/OpenAPI JSON with tools like drf-spectacular. This allows us to test the majority of API endpoints automatically - with our own software we systematically test all routes, methods and parameters for authorization issues.
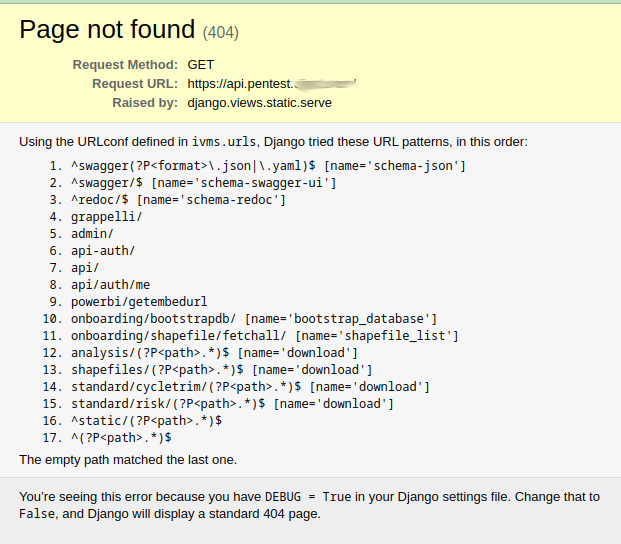
When DEBUG=True is active in production, Django provides the complete URL conf on 404s and exceptions - perfect for pentesters to find "hidden" or "forgotten" endpoints. This saves fuzzing time and massively increases the effectiveness of the pentest.
The price depends on complexity - simple Django apps vs. complex DRF APIs with custom permissions make the difference.
For standard Django apps
For API-heavy Django projects
Our Mini Pentest for Django checks the most critical vulnerabilities: DEBUG mode in production, DRF authorization, ORM SQL injections and CSRF protection. Ideal for quick pre-release checks or as an entry into regular security testing.
Focused examination of the most critical vulnerabilities
Transparent fixed price - no hidden costs
Fast, actionable reporting as ticket list
Popular add-ons:
We've had the privilege of working with some of the world's leading companies and strengthening their IT security.








Have questions about our services? We'd be happy to advise you and create a customized offer.
We'll get back to you within 24 hours
Your data will be treated confidentially
Direct contact with our experts
